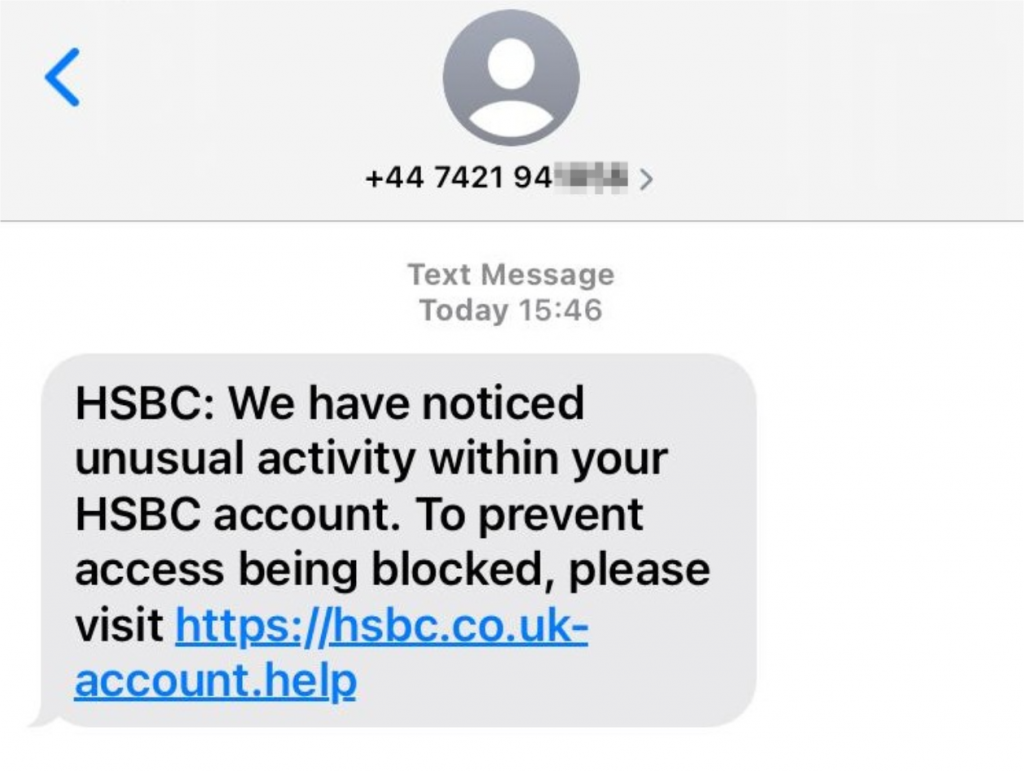
Key Identifiers In A Phishing Email . Every data breach and online attack seems to involve some kind of phishing. how to recognise a phishing email. we explain how to recognize each type of threat. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. There are key signs that can make it obvious that the email is just an attempt. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information.
from www.cscdbs.com
how to recognise a phishing email. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. There are key signs that can make it obvious that the email is just an attempt. Every data breach and online attack seems to involve some kind of phishing. we explain how to recognize each type of threat. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the.
Phishing Scams How to Spot Them and Stop Them CSC
Key Identifiers In A Phishing Email Every data breach and online attack seems to involve some kind of phishing. There are key signs that can make it obvious that the email is just an attempt. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. how to recognise a phishing email. we explain how to recognize each type of threat. Every data breach and online attack seems to involve some kind of phishing.
From mungfali.com
Identifying Phishing Emails Key Identifiers In A Phishing Email how to recognise a phishing email. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. There are key signs that can make it obvious that the email is just an attempt. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not. Key Identifiers In A Phishing Email.
From us.norton.com
How to protect against phishing 18 tips for spotting a scam Key Identifiers In A Phishing Email how to recognise a phishing email. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. Every data breach and online attack seems to involve some kind of phishing. we explain how to recognize each type of threat. phishing detection is the process of identifying phishing. Key Identifiers In A Phishing Email.
From oxygentechnologies.ca
10 Common Traits of Phishing Emails Oxygen Technical Services Ltd Key Identifiers In A Phishing Email in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. how to recognise a phishing email. phishing detection is the process of identifying phishing attacks in their. Key Identifiers In A Phishing Email.
From arstechnica.com
Torrent of imagebased phishing emails are harder to detect and more Key Identifiers In A Phishing Email Every data breach and online attack seems to involve some kind of phishing. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. how to recognise a phishing email. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to. Key Identifiers In A Phishing Email.
From techgen.com
8 Ways to Identify a Phishing Email TechGen Key Identifiers In A Phishing Email in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. we explain how to recognize each type of threat. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. There are key signs that can make it obvious. Key Identifiers In A Phishing Email.
From zcybersecurity.com
7 Phishing Awareness Email To Employees 2023 Phishing Awareness Email Key Identifiers In A Phishing Email phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. how to recognise a phishing email. Every data breach and online attack seems to involve some kind of phishing. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent. Key Identifiers In A Phishing Email.
From www.mtechsystems.co.uk
Top Tips for Spotting Phishing Emails Cyber Security Key Identifiers In A Phishing Email how to recognise a phishing email. There are key signs that can make it obvious that the email is just an attempt. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. in today’s digital world, phishing emails are one of the most common tactics used. Key Identifiers In A Phishing Email.
From www.cio.com
What is phishing? How this cyber attack works and how to prevent it Key Identifiers In A Phishing Email in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. we explain how to recognize each type of threat. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. key indicators of phishing emails include. Key Identifiers In A Phishing Email.
From www.netatwork.com
8 Tips for Detecting a Phishing Email IT and Email Security Tips Key Identifiers In A Phishing Email key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. There are key signs that can make it obvious that the email is just an attempt. how to. Key Identifiers In A Phishing Email.
From mavink.com
How To Identify Phishing Emails Key Identifiers In A Phishing Email key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. There are key signs that can make it obvious that the email is just an attempt. how to recognise a phishing email. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals. Key Identifiers In A Phishing Email.
From almanca.com.tr
What is a phishing attack? Cloud Blog Key Identifiers In A Phishing Email There are key signs that can make it obvious that the email is just an attempt. how to recognise a phishing email. we explain how to recognize each type of threat. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. Every data breach and online attack. Key Identifiers In A Phishing Email.
From www.ts.vcu.edu
How do I identify a phishing scam? Technology Services VCU Key Identifiers In A Phishing Email how to recognise a phishing email. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. There are key signs that can make it obvious that the. Key Identifiers In A Phishing Email.
From www.ne-inc.com
How To Identify Phishing Emails Key Identifiers In A Phishing Email in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. Every data breach and online attack seems to involve some kind of phishing. There are key signs that can make it obvious that the email is just an attempt. phishing detection is the process of identifying phishing attacks. Key Identifiers In A Phishing Email.
From infusetech.co.uk
How to prevent phishing attacks 8 signs of a scam email Key Identifiers In A Phishing Email phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. There are key signs that can make it obvious that the email is just an attempt. how. Key Identifiers In A Phishing Email.
From www.cscdbs.com
Phishing Scams How to Spot Them and Stop Them CSC Key Identifiers In A Phishing Email how to recognise a phishing email. key indicators of phishing emails include generic greetings, spelling and grammar mistakes (although not always), and urgent or threatening. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. There are key signs that can make it obvious that the. Key Identifiers In A Phishing Email.
From www.apexcomputing.co.uk
Tips for Detecting a Phishing Email Apex Computing Key Identifiers In A Phishing Email in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information. we explain how to recognize each type of threat. how to recognise a phishing email. Every data breach and online attack seems to involve some kind of phishing. key indicators of phishing emails include generic greetings,. Key Identifiers In A Phishing Email.
From securityboulevard.com
AIGenerated Phishing Emails Security Boulevard Key Identifiers In A Phishing Email Every data breach and online attack seems to involve some kind of phishing. There are key signs that can make it obvious that the email is just an attempt. we explain how to recognize each type of threat. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information.. Key Identifiers In A Phishing Email.
From blog.teamascend.com
Don’t Get Hooked! 7 Signs of a Phishing Email Key Identifiers In A Phishing Email how to recognise a phishing email. we explain how to recognize each type of threat. phishing detection is the process of identifying phishing attacks in their early stages, warning users and administrators, and ideally, mitigating the. in today’s digital world, phishing emails are one of the most common tactics used by cybercriminals to steal personal information.. Key Identifiers In A Phishing Email.